Upsurge in the tourism industry after the COVID-19 pandemic grabs the attention of cybercriminals to scam the tourists.
Researchers are warning a post-COVID upsurge in travel has painted a bullseye on the travel industry and has spurred related cybercrimes.
Criminal activity includes an uptick in adversaries targeting the theft of airline mileage reward points, website credentials for travel websites and travel-related databases breaches, according to a report by Intel 471.
The impact of the attacks are hacked accounts stripped of value. But also, researchers say the consequences of recent attacks can also include flight delays and cancelations as airlines grapple with mitigating hacks.
Your Reward Points Head to Illicit Markets
Since January the researcher at Intel 471 detect multiple hacks used by cybercriminals to trade the credentials linked to the traveling websites.
The threat actors were specifically interested in “mileage rewards accounts with at least 100,000 miles,” according to 471. These accounts are used to earn certain rewards on every dollar that is spent. The account credentials that were listed in February belong to U.K.-based users from a major traveling website and two U.S.-based airlines.
“Access to these accounts allowed actors to leverage the rewards to book travel reservations for themselves and other customers,” said researchers. “The accounts and their respective rewards points could be resold to other actors looking to conduct similar types of travel fraud activity,” they added.
The exploitation of rewards-points programs, especially those associated with travel, is not new. Researchers have tracked several incidents over the years where hackers have targeted reward points. In 2018, a pair of Russian teens have been arrested for infiltrating more than a half-million online accounts, in particular targeting services that offer rewards points.
Researchers point out that as the travel industry rebounds from a COVID-related slump, the industry is once again a prime target for cybercriminals.
Travel-related Identity Theft
Other criminal activities include the targeting of travel-related databases – ripe with employee and traveler personal identifiable information (PII) that threat actors can sell for money.
Researchers observed on travel-related hackers leveraging a database of “40,000 people employed in Illinois”. The stolen database includes PII of employees. Researchers said this type of leaked information plays a role in travel-related fraud – allowing an attacker to generate new identities that can be used to either cross boarders or evade authorities.
In one instance, Intel 471 researchers, cybercriminals used PII to create illicit travel documents used for border crossings. “Shortly after the start of the (Russian invasion of Ukraine) war, the actor claimed the insider could facilitate illegal border crossings for Ukrainian males aged 18 to 60” researchers noted.
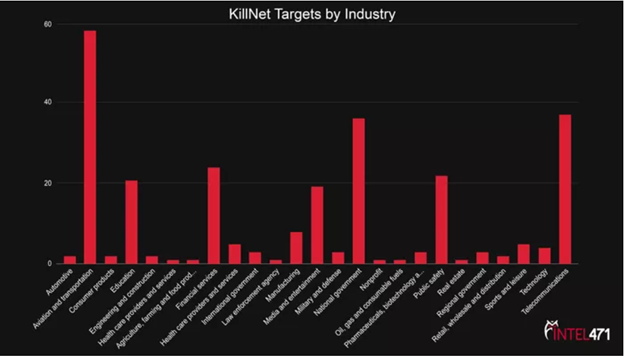
Some of the traveling bodies including Romania-based Air Traffic Services Administration and Bucharest Airport were targeted by a pro-Russian group of hackers known as KillNet. “Aviation and transportation entities were among KillNet’s most frequented targets in the first half of 2022,” researcher added.
Last month, an attack on the IT systems of SpiceJet airlines left travelers stranded at airports and causes the delay and cancellation of flights.
Protection From the Scams
The researchers suggested customers stay vigilant while making arrangements and should book flights from a trusted source, handle payment cautiously, and refrain from getting phished in any dubious vacation-related offers.Write a comment
Share this article:
SUGGESTED ARTICLES

Voicemail Scam Steals Microsoft Credentials
Attackers are targeting a number of key vertical markets in the U.S. with the active campaign, which impersonates the organization and Microsoft to lift Office365 and Outlook log-in details.June 21, 2022

Facebook Messenger Scam Duped Millions
One well crafted phishing message sent via Facebook Messenger ensnared 10 million Facebook users and counting.June 16, 2022

Office 365 Config Loophole Opens OneDrive, SharePoint Data to Ransomware Attack
A reported a “potentially dangerous piece of functionality” allows an attacker to launch an attack on cloud infrastructure and ransom files stored in SharePoint and OneDrive.June 21, 2022

Voicemail Scam Steals Microsoft Credentials
Attackers are targeting a number of key vertical markets in the U.S. with the active campaign, which impersonates the organization and Microsoft to lift Office365 and Outlook log-in details.June 21, 2022

Facebook Messenger Scam Duped Millions
One well crafted phishing message sent via Facebook Messenger ensnared 10 million Facebook users and counting.June 16, 2022

Office 365 Config Loophole Opens OneDrive, SharePoint Data to Ransomware Attack
A reported a “potentially dangerous piece of functionality” allows an attacker to launch an attack on cloud infrastructure and ransom files stored in SharePoint and OneDrive.June 21, 2022

Voicemail Scam Steals Microsoft Credentials
Attackers are targeting a number of key vertical markets in the U.S. with the active campaign, which impersonates the organization and Microsoft to lift Office365 and Outlook log-in details.June 21, 2022

Facebook Messenger Scam Duped Millions
One well crafted phishing message sent via Facebook Messenger ensnared 10 million Facebook users and counting.June 16, 2022
DISCUSSION
Leave A Comment
This site uses Akismet to reduce spam. Learn how your comment data is processed.
INFOSEC INSIDER
- Gamification of Ethical Hacking and Hacking EsportsJune 22, 2022
- Ransomware Risk in Healthcare Endangers PatientsJune 16, 2022
- Taming the Digital Asset TsunamiJune 8, 2022 1
- Cyber Risk Retainers: Not Another Insurance PolicyJune 7, 2022 1
- Cybercriminals Expand Attack Radius and Ransomware Pain PointsJune 2, 2022
Newsletter
Subscribe to Threatpost Today
Join thousands of people who receive the latest breaking cybersecurity news every day.Subscribe nowTwitter
Researchers have discovered that a
